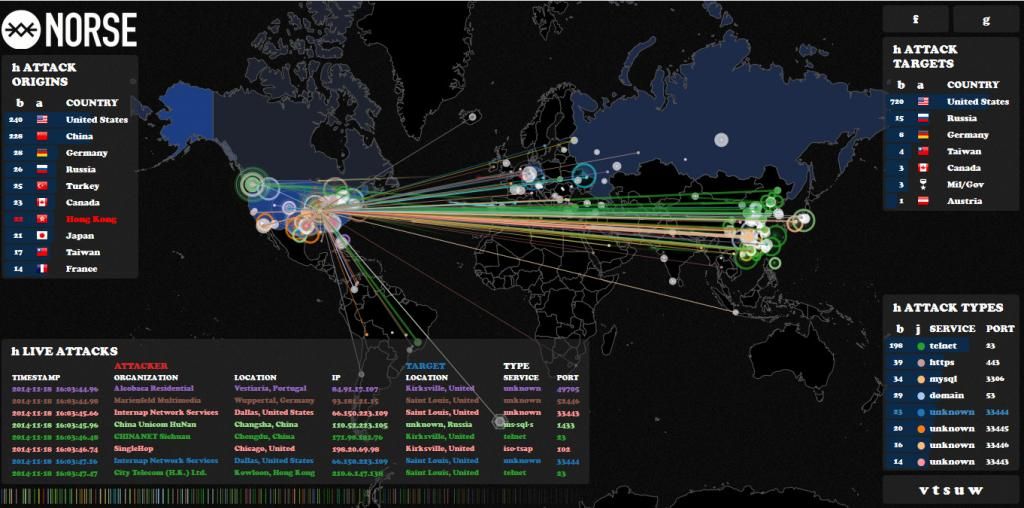
How big of a threat is there right now on your private data? The news seems to be constantly beating the drum of a new hack or imminent threat. While some of it can by hype for a slow news day, there is truth in that we are under attack every single day (as evidenced by eBay, HomeDepot and Target from just this last year). Check out the live map from IP Viking to get an idea of what’s currently going on around the world.
Unfortunately, though with the news cycle as it is, we often don’t see any resolution to these problems. I just wanted to take a few minutes to review the latest “problems” that have been reported and see where we are today in making ourselves safer.
Masque Attack
This is from the most recent bit of news. Masque Attack is specially crafted to iOS users (iPad, iPhone, etc…). It can only infect your device if you download software from some place other than the Apple App Store.
What You Should Do – Nothing. Just buy your apps from the App Store and you’ll have nothing to worry about.
Poodle
Probably because of the name and by the time it was reported, we just were numb to this one. Its an attack towards SSL (the secure lock icon in your browser).
What You Should Do – Nothing. Some experts report that this attack is very difficult to pull off, if not impossible. The steps necessary assume that the attacker has control of the system already.
Darkhotel
These are attacks on business people traveling in the Asia area. When connected to hotel wifi, you are usually asked to enter your name and room number to grant access. At this step, attackers are sifting through the supplied info to see if it is a target worth spying upon. If it is, a pop-up window is displayed notifying the user that they need to update some piece of software (such as flash). Doing so will install the spying software.
What You Should Do – NEVER install anything from the web when not at home or your office on a trusted network. This and other mischievous/damaging things can be easily done on public wi-fi networks. This includes networks which you may even pay for, such as a coffee shop or hotel.
Shellshock
This vulnerability was found in the BASH system used by Unix type operating systems. It allowed attackers to put their own code into the computer and perform just about any function desired. In order for the attack to work, the computer being attacked had to employ one or more of the following routines:
CGI – web server, Open SSH, a rouge DHCP server, qmail or the IBM HMC
What You Should Do – If you don’t know what any of the previous stuff is, do nothing. If you are running a service from the list above, you should have updated already and be patched. (The tricky part is ensuring someone doesn’t hop on your network and operate a poison DHCP server….but that’s for the sysadmins to worry about.)
Heartbleed – Similar to Poodle as listed above in that it targeted secure internet connections.
What You Should Do – Nothing. All systems by now should be patched.
BadUSB – This one has the potential to be really bad. It is an infection which is spread by USB devices. Because it infects the firmware of the USB device, antivirus software does not see it. Once the device is plugged into a computer, it performs its deed in the background, quite possibly without you ever knowing. But wait, there’s more! Now you have the infection on your computer and each USB device you plug in now gets infected as well and is able to spread to other computers as the USB device is shared. Where this will probably have the most effect is with USB memory sticks/USB flash drives.
What You Should Do – Don’t get too hostile yet, as no known attacks have used this methodology yet in the public. So far it has only been experimental. But it is possible and not very difficult. So try not to share USB devices with strangers. Suggest cloud storage instead, to share files (though nothing sensitive/secret, since your connections will probably be in the clear and susceptible to spying). Hopefully, the manufacturers will soon release devices which either lock the firmware or require signed keys to alter it. Because how many times have you updated the firmware on your mouse?
One Last Consideration – Setup a VPN
A VPN (Virtual Private Network) allows you to communicate to a network with a secure and encrypted connection. So, say you are at that suspicious hotel and you need to check you company email. If you connect to the VPN first, you can be sure that there are no men in the middle spying on your corporate secrets. Or even personally, when you are at the coffee shop and need to check your bank account balance, using a VPN keeps you safe. It also provides the added benefit of not showing anyone your current location. All activity looks like it is coming from the VPN computer you are connected to at that time. (I like this especially since I have Verizon so I can dodge their perma-cookies, but since I am VPNed to the computer at my house, I still can easily access gmail and other secured connections without hassle as that computer is already trusted.)
There are services which offer VPN service, some even for free. I am personally wary of these services. I haven’t heard anything bad come from them yet, but its just not something I’m willing to trust yet. ALL of your internet traffic is going to go through this VPN and they can potentially see everything that you are doing (and maybe even save it).
If your company doesn’t offer VPN access, make a request to the IT folks. It may already be there and you not know it. They should be eager to help you get setup if you ask nicely, because it will only make their job easier in the end knowing that your computer is more secure.
At home, if you have a computer sitting around not doing much, setup your own. It’s not too difficult and wise to keep work stuff at work and home stuff at home. If you have a Windows PC, check out this link:
http://www.practicallynetworked.com/security/set-up-a-personal-windows-vpn.htm
or, if you have a Mac, then go this route:
Either way, do what you can to keep your data yours and out of the hands of others.